United Airlines recently rewarded two hackers for finding security breaches in the airline’s computer system by giving them each one million frequent-flier miles. Wait, isn’t hacking a bad thing? Should incentives be used to dissuade hackers—or should companies be proactively adopting higher security measures within the network to protect customer and company assets?
Setting a new precedent for the transportation industry, United recently hosted a “bug bounty” award for computer programmers to identify possible security breaches in company infrastructure before a “real” hacker has the chance to do so. It’s an incentive driven way for companies to enlist the hacking expertise of coders who are looking not to steal a bunch of classified information, but to cash in on some pretty hefty prizes. United’s contest promised rewards on a tier system: bugs identified in third-party structures would receive 50,000 miles in compensation, exploits that could compromise customer information earned 250,000 miles, and major remote-code execution flaws would earn so called “white hat hackers” the jackpot prize of 1,000,000 frequent-flier miles.
By adopting the bug bounty competition method, United received valuable information about fortifying its online security measures before that information could get into the wrong hands. And while a million frequent flier miles can get you around the world five times over, awarding that kind of life-changing prize isn’t costing United much of anything. It’s a win-win for United in terms of forward thinking publicity, and a win for coders who’ve caught the travel bug.
The bug bounty model was first conceived by engineer Jarrett Ridlinghafer in 1996, when he was working at Netscape Communications. Based on Netscape’s success in leveraging coding expertise through this new model of incentives, tech giants including Facebook and Google quickly followed suit. United Airlines is the first in the airline and transportation industry to extend a similar offer to white hat hackers. One of the winners, Jordan Wiens of Florida, had never entered a bug bounty competition before, and considered the hacks he identified as minor in nature. Imagine his surprise when he won the 1,000,000 miles, not to mention some good publicity for his online security company, Vector35.
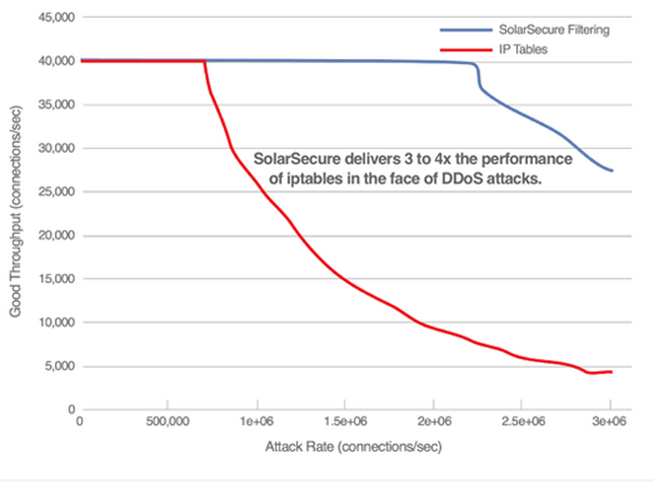
In the future, we can expect to see a growing trend of companies rewarding programmers who expose their system flaws for rewards. It sure beats the alternative outcome that we’ve seen in recent months at companies like Home Depot and Target. A far better solution would be for more companies to proactively adopt higher security measures within the network to protect customer and company assets, like those offered by SolarFlare. Integrated into network servers – usually the primary target of cyber attacks – the SolarSecure Filter Engine mitigates attacks with a high performance packet filter engine, allowing for a higher degree of monitoring and securing data without having to add additional hardware. The better a company’s ultimate line of defense against potential hackers, the better its customers will feel about their cyber security.
Images via Flickr/elhombredenegro;SolarFlare