It’s hard to look at the news lately without seeing another story about an international corporation dealing with a massive security breach. 2014 attacks at Sony and JPMorgan Chase stole the headlines, while 2015 has brought major headaches to Ashley Madison. Most recently, the breach at British telecom firm TalkTalk—which potentially compromised 4 million users’ sensitive bank data— highlights larger issues that all enterprises must actively work to safeguard against.
 As details continue to emerge about the massive DDoS attack on TalkTalk’s server, the company is taking heat for disregarding security vulnerabilities that were raised in the past. Ashley Madison’s hack was also the result of weak security measures that relied on encrypted passwords. These breaches should all serve as serious warnings to enterprises to beef up their security measures to protect not only their own sensitive data, but also that of their customers.
As details continue to emerge about the massive DDoS attack on TalkTalk’s server, the company is taking heat for disregarding security vulnerabilities that were raised in the past. Ashley Madison’s hack was also the result of weak security measures that relied on encrypted passwords. These breaches should all serve as serious warnings to enterprises to beef up their security measures to protect not only their own sensitive data, but also that of their customers.
From DDoS attacks to embedded approaches like phishing or malware, hacking methods continue to evolve. Traditionally, enterprises have focused on fortifying the perimeter to mitigate attacks. But large amounts of data pass through network sub-systems, meaning that every level of the server should be protected. A company’s best line of defense is in implementing low latency, high-frequency packet capture solutions to increase security not only on the perimeter, but at the top of every rack or within every server.
Solarflare’s approach to security is to assume that attacks will happen. But instead of letting an intruder have access to the entire castle just because they crossed the moat, Solarflare’s packet capture approach adds a new layer of protection at the server level. Think of it as a series of safes, locking your valuables up separately to prevent unwelcome visitors from running off with all the crown jewels.
The core of Solarflare’s DDoS attack mitigation consists of a high performance packet filter engine that uses a pseudo-microcode instruction set to configure the filter engine to selectively accept, reject or rate-limit packets based on packet headers and packet contents. The microcode used for filtering is under user control, making the filtering behavior highly configurable. This packet capture approach allows “bad” traffic to be detected very early in the network stack, so DDoS attacks can be absorbed without degradation of “good” traffic. The filter engine provides the ability to efficiently block or rate limit packets based on their contents, as well as request level deep packet inspection. For example, HTTP requests can be inspected and connections aborted dependent on the contents of the HTTP headers.
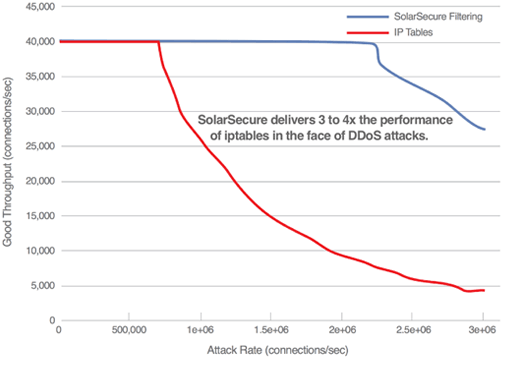
In the face of DDoS attacks, servers enabled with the SolarSecure Filter Engine were found to be 3 to 4 times more effective at packet filtering than iptables. This is a great way to identify and slow down potential threats before situations escalate to the disastrous level that TalkTalk is now facing.
The second phase of protection involves internal network segmentation. Multitenant cloud environments help defend against the spread of threats across the entire network. Partitioning off infected areas, new policies, filters and access control lists can be implemented to protect critical data from unauthenticated users.
The future of network security—and the best way to stay one step ahead of potential hacks— is in this multi-layered packet capture approach. As large enterprises continue to be targeted by evolving hacking methods, a multilayered defense plan at the server level is essential.

